1. Image Scanning
- Code from untrusted registries
- Vulnerabilities in tools of OS or libraries
- Eliminate unnecessary dependencies
- Use leaner base images
Tools
- snyk
- sysdig
- scan image before pushing it to the registry
- Check for vulnerabilities and misconfigurations
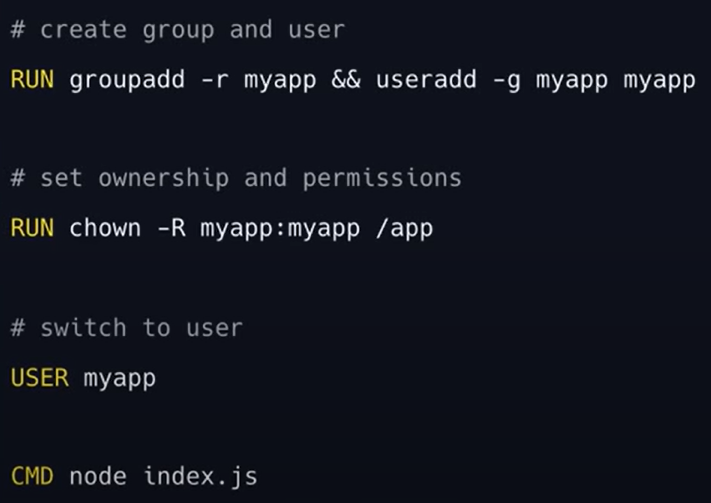
2. Run as Non-Root User
- Create a dedicated user and group
- Change to non-root user with USER directive
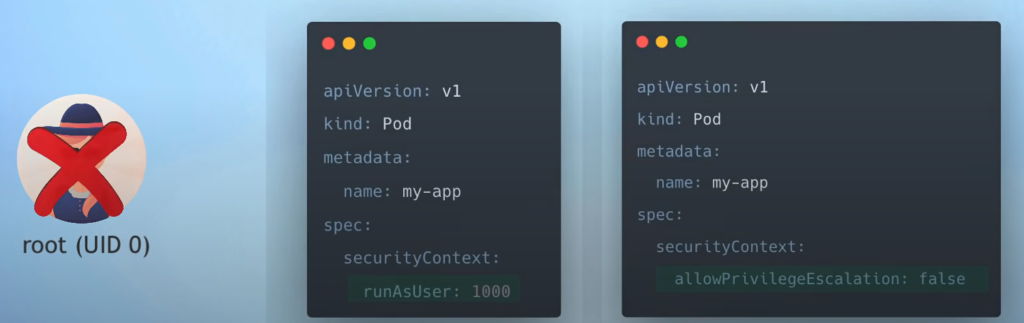
3. User and Permissions – Use RBAC to manage access permissions
- Authentication
- Authorization
- Apply Least Privilege Rule
RBAC – Role Based Access Control applies to a specific namespace
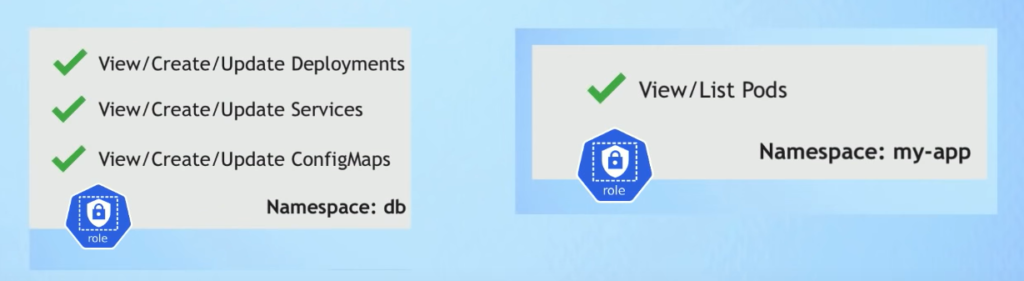
Role-Binding: Bind a Role to a User or Group
CulsterRole: cluster wide
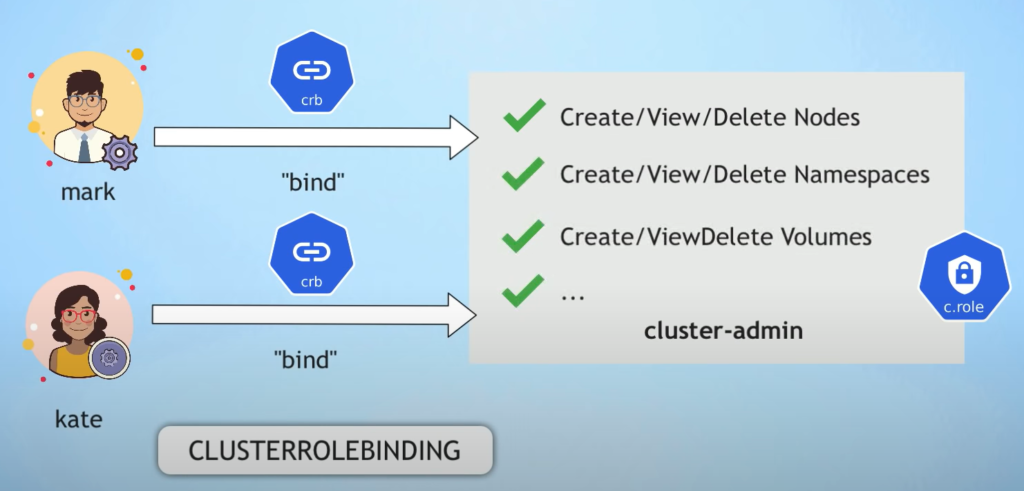
For non-human: use ServiceAccount (sa), which represents an Application User
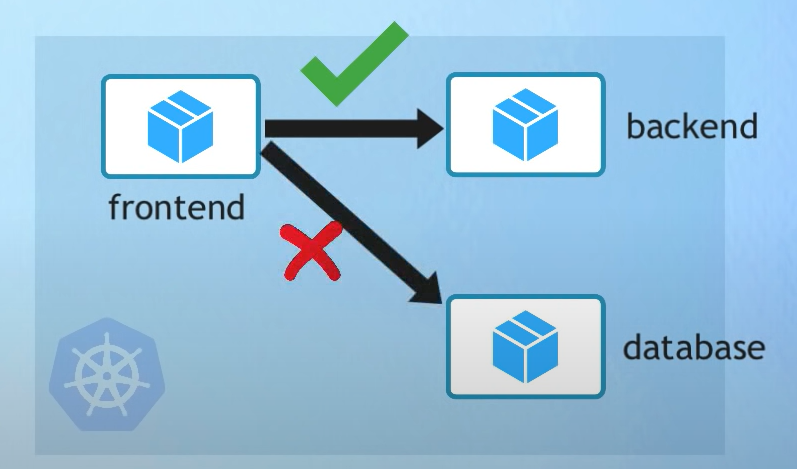
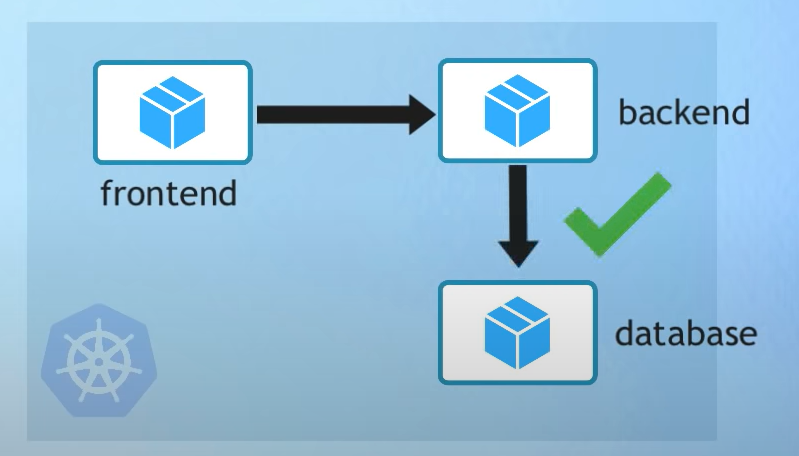
4. Use Network Policies on network level / Service Mesh on service/application level
- Pod can talk to any Pod in Cluster
- Use NetworkPolicy to limit the communication and create Network Rules (FE can talk to BE but not DB directly)
- Apply Least Access Allowed Rules
5. Encrypt communication
- By default, communication between pods is unencrypted
- Use ServiceMesh to enable mTLS (mutual TLS) between pods
6. Secure Secret data
- By default is not secure, as stored unencrypted, only base64 encoded
- Anyone with permission to view Secrets can read it
echo YWxrb2xvLmNvbQ== | base64 --decodeTools:
- enable encryption using EncryptionConfiguration resource
- AWS KMS
- HashiCorp Vault
7. Secure etcd store
- etcd stores cluster configuration data (manifest files for k8s resources)
- Put etcd behind firewall
- Encrypt etcd data
8. Backup and Restore
- Have automated Backup and Restore
9. Configure Security Policies
- for admin
- for others: dev, qa..
- Define Policies to enforce specific configurations
- don’t allow pods that run containers with root
- network policy needs to be defined for every pod
- Tools: Open Policy Agent, Kyverno (via “Admission Controller”, automated validations)
10. Disaster Recovery
- Have proper strategy and mechanism
- Automated & well tested recovery plan
- minimal affect on users
Tools: K10
