Flow Logs capture information about the IP traffic going to and from network interfaces in a VPC.
Publishes the flow log records to:
- S3 bucket (log file object)
- CloudWatch Logs (log stream)
Levels
- VPC
- Subnet
- Network Interface
If created for a subnet or VPC, each network interface in that subnet or VPC is monitored.
Limitations
- Can’t enable flow logs for VPC’s that are peered, unless the peer VPC is in your account
- Flow log configuration can’t be changed after it’s been created
Monitoring
Not all traffic is monitored, e.g. the following traffic is excluded:
- Traffic that goes to Route53.
- Traffic generated for Windows license activation.
- Traffic to and from 169.254.169.254 (instance metadata).
- Traffic to and from 169.254.169.123 for the Amazon Time Sync Service.
- DHCP traffic.
- Traffic to the reserved IP address for the default VPC router.
Log
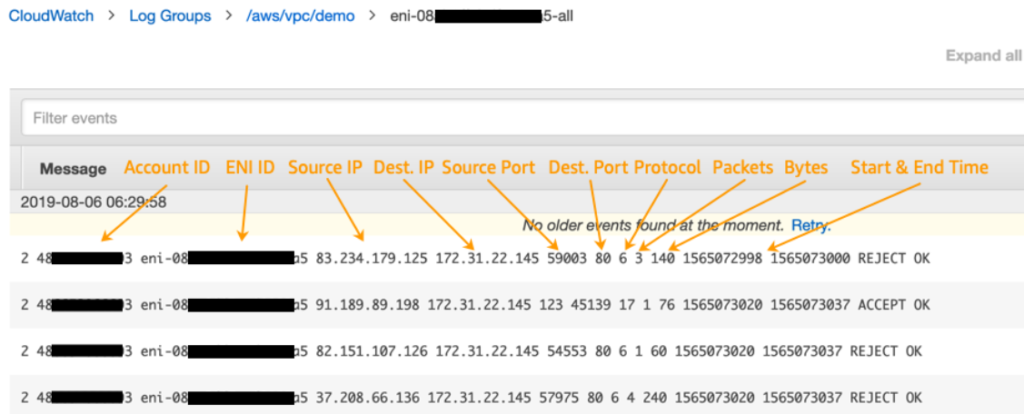
Create a VPC Flow Log using CLI
aws ec2 create-flow-logs --resource-type VPC \
--region eu-west-1 \
--resource-ids vpc-12345678 \
--traffic-type ALL \
--log-destination-type s3 \
--log-destination arn:aws:s3:::sst-vpc-demo \
--log-format '${version} ${vpc-id} ${subnet-id} ${instance-id} ${interface-id} ${account-id} ${type} ${srcaddr} ${dstaddr} ${srcport} ${dstport} ${pkt-srcaddr} ${pkt-dstaddr} ${protocol} ${bytes} ${packets} ${start} ${end} ${action} ${tcp-flags} ${log-status}'https://aws.amazon.com/blogs/aws/learn-from-your-vpc-flow-logs-with-additional-meta-data/
