doc:
Share an encrypted AMI between accounts and launch an encrypted, EBS backed EC2 instance from the shared AMI.
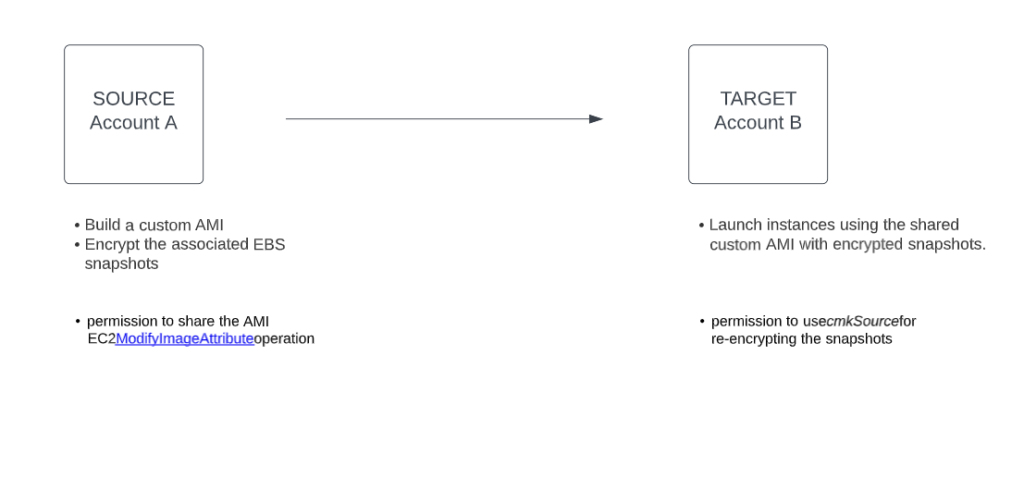
Create policy for the source account
- permission to share the AMI EC2 ModifyImageAttribute operation
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2: ModifyImageAttribute",
],
"Resource": [
"arn:aws:ec2:us-east-1::image/<12345678>"
]
}
]
}Create policy for the target account
Permission to use cmkSource for re-encrypting the snapshots. Will actually add the target account’s ID to the cmkSource key policy.
1. In source account, go to KMS / Customer Managed Keys, select (cmkSource)
2. In other AWS account, select Add other AWS accounts
3. In the arn:aws:iam:: field, enter the target account ID
4. Select Add another AWS account
Create policy for the target account
Perform the following AWS KMS operations on cmkSource in order to launch an instance from a shared encrypted AMI:
- DescribeKey
- CreateGrant
- ReEncrypt*
- Decrypt
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"kms:DescribeKey",
"kms:ReEncrypt*",
"kms:CreateGrant",
"kms:Decrypt"
],
"Resource": [
"arn:aws:kms:us-east-1:<111111111111>:key/<key-id of cmkSource>"
]
}
]
}Sharing the AMI with CLI
aws ec2 modify-image-attribute \
--image-id <ami-12345678> \
--launch-permission "Add=[{UserId=<999999999999>}]"Launch an instance from the shared encrypted AMI
aws ec2 run-instances \
--image-id ami- \
--count 1 \
--instance-type m4.large \
--region us-east-1 \
--subnet-id subnet-aec2fc86 \
--key-name 2016KeyPair \
--security-group-ids sg-f7dbc78e subnet-id subnet-aec2fc86 \
--block-device-mappings file://mapping.jsonWhere mapping.json:
[
{
"DeviceName": "/dev/xvda",
"Ebs": {
"Encrypted": true,
"KmsKeyId": "arn:aws:kms:us-east-1:<999999999999>:key/<abcd1234-a123-456a-a12b-a123b4cd56ef>"
}
}
]